What Is Fraud Protection And How Does It Work?

Think of fraud protection as a digital bodyguard for your financial life. It’s not just a single tool or app, but a whole system of security layers designed to spot and stop threats before they can do any damage. It’s all about keeping your money and personal data safe from anyone who shouldn't have access.
What Is This Digital Bodyguard Doing?

Just like a home security system uses cameras, alarms, and locks to keep your house safe, fraud protection uses a mix of smart technology and well-defined processes. Its main job is to constantly watch for suspicious activity, double-check that you are who you say you are, and immediately shut down potential threats. It's a silent partner, always running in the background.
This defense system is crucial. Every single time you log into an account, buy something online, or send money, these systems are quietly at work, confirming that the action is genuinely yours. They get to know your normal patterns—like where you typically shop and how much you usually spend—so they can spot something out of the ordinary in a split second.
The Core Layers of Fraud Protection
A truly strong system isn't just one wall; it's a fortress with multiple layers of defense working together. Each one serves a different purpose, creating a robust shield against all sorts of scams and unauthorized access.
The table below breaks down these essential functions into a simple framework.
| Security Layer | What It Does | Analogy |
|---|---|---|
| Proactive Monitoring | Constantly scans your accounts for unusual patterns or red flags. | The security camera that never sleeps, always watching for trouble. |
| Identity Verification | Confirms you are who you say you are before granting access. | The bouncer at the door, checking IDs to make sure only the right people get in. |
| Instant Response | Immediately blocks suspicious transactions or locks an account. | The alarm system that goes off, scaring away an intruder the moment they try to break in. |
This layered strategy is what makes modern security so effective. It’s much harder for a criminal to get through a series of defenses than it is to bypass a single lock.
By combining these elements, platforms like DIYAuctions create a powerful defense mechanism for both buyers and sellers. To learn more about keeping your online activities secure, check out the great resources in our learning center.
The Modern Threat Landscape: Why Protection Is Essential

Not too long ago, the biggest online threat most of us worried about was a suspicious email from a Nigerian prince. Times have definitely changed. Today’s fraudsters run their operations like global corporations, armed with sophisticated tools to pull off complex scams that are harder than ever to spot.
They don’t just target one person at a time. They use automated systems to launch widespread attacks, probing for any weakness across millions of accounts at once. In this new reality, relying on old habits like a strong password is like bringing a simple padlock to a high-tech bank heist. It's just not enough anymore.
The Scale of Modern Fraud
The numbers are staggering. Global losses from these scams now top $1 trillion every single year. Worse yet, only about 4% of victims ever see their money again.
A big reason for this is that criminals are now using artificial intelligence (AI) to make their schemes more believable and to scale up their attacks. You can see more on these evolving fraud trends at datavisor.com.
The modern fraudster isn't just a lone operator; they are part of a connected network using sophisticated technology. This shift requires an equally sophisticated defense to protect your assets and identity.
Common Threats Everyone Faces
This new environment creates very real risks for everyone, from individual sellers to large marketplaces. Here are a few of the most common threats you’ll see out there:
- AI-Powered Scams: Scammers use AI to create incredibly realistic deepfake videos or voice clones. They can impersonate a family member in distress or a company executive, making urgent and convincing requests for money.
- Account Takeover (ATO): This is a huge one. Criminals get their hands on credentials from other data breaches and use them to break into your accounts, often to steal money or your identity.
- Phishing and Smishing: The classic email and text message attacks are still around, but they’ve gotten much smarter. Fraudsters can now send deceptive messages that perfectly mimic legitimate companies, tricking you into giving up your sensitive info.
Understanding these threats makes it clear why having a robust fraud protection strategy is no longer optional. It's essential. At DIYAuctions, we make this a top priority to safeguard every transaction and every user on our platform. You can read more about our commitment to user privacy and how we protect your data.
How Fraud Protection Systems Work Behind The Scenes
Ever wonder what happens in those few seconds between clicking 'buy' and getting an order confirmation? It feels instant, but a whole lot of security work is happening in the background to make sure you're the one making the purchase.
Think of it like a silent, high-tech security detail. A team of specialists springs into action, each with a specific job, all working together to verify your transaction is legitimate. It’s a multi-layered process that has to be both lightning-fast and incredibly smart.
This flow chart gives a bird's-eye view of how these systems stop threats in their tracks.
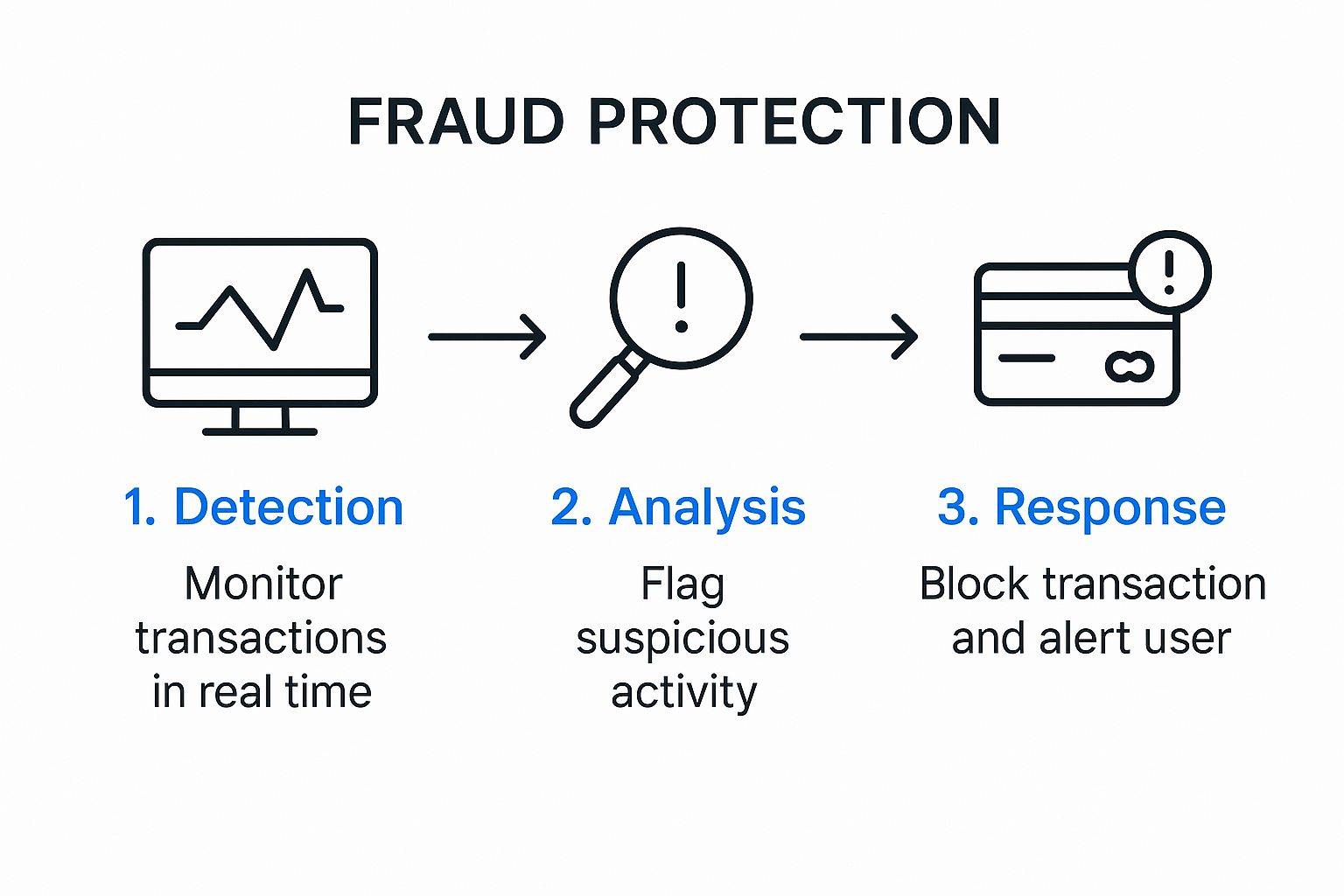
As you can see, it all starts with monitoring, moves to analysis, and finishes with a clear response. This all happens in a blink of an eye for every single transaction on our platform.
The Security Team in Action
Let's meet the key players on this invisible security team and see what each one does. Each role is like a different agent, contributing their expertise to the mission of stopping fraud before it happens.
-
Data Monitoring (The Lookout): This is the first line of defense. It’s constantly scanning for anything that looks out of place—like a login from a new device halfway across the world or a purchase that’s 10 times larger than your average bid. It’s always on the lookout for red flags.
-
Behavioral Analytics (The Profiler): This layer gets personal. It learns your typical habits over time, like the devices you usually bid from, the time of day you're most active, or even your typical bidding patterns. If someone’s behavior suddenly deviates from your profile, it immediately raises an alarm.
-
Identity Verification (The Gatekeeper): This is the agent who asks for your ID. It uses things like your password, two-factor authentication codes sent to your phone, or biometrics to confirm you are who you say you are before letting you proceed.
These systems don't work alone. They're constantly talking to each other, sharing data to build a complete risk profile for every single action you take. It's this teamwork that makes the system so good at catching even the most clever fraud attempts.
All of this information funnels into one final, crucial step.
Making the Final Call with Transaction Scoring
The last piece of the puzzle is Transaction Scoring, which acts as the 'risk analyst.' This system gathers all the intelligence from the other layers and assigns a real-time risk score to every login or transaction.
A low score means everything looks normal, and the action is approved instantly.
A high score, on the other hand, triggers an immediate response. That might mean blocking the transaction entirely, asking for extra verification, or sending you a security alert. It's the final, decisive move that keeps fraudsters out and your account secure.
Seeing Through the Scams: How Protection Works in the Real World

It’s one thing to talk about fraud protection technology, but it’s another thing entirely to see how it stands up against actual, real-world scams. Think of these systems as digital guardrails, specifically designed to protect your money and information from the kinds of fraud that are becoming alarmingly common.
From fake invoices to hijacked accounts, scammers are always finding new angles. And the numbers don't lie. A recent survey found that a staggering 79% of organizations were hit by payments fraud in 2024. That same report showed that Business Email Compromise (BEC) was the most common type of attack. If you want to dive deeper, you can explore the full payments fraud survey here.
These statistics aren't just numbers on a page; they represent a real and urgent threat that requires a powerful defense.
Beating the Scammers at Their Own Game
Let’s walk through a couple of common scenarios to see exactly how these defenses work. Each one is a direct counter-move to a criminal's playbook.
-
Scenario #1: The Fake Invoice Ploy A scammer gets into an employee’s email and fires off a phony invoice to the finance department. The email demands an urgent payment to a new, unfamiliar bank account.
- The Defense in Action: An automated payment verification system immediately flags the request. It notices the recipient's bank details don't match any approved vendors in the system, and the "urgent" demand trips a high-risk sensor. The transfer is automatically blocked, and a manager is alerted to review it, stopping the fraud before a single dollar is lost.
-
Scenario #2: The Account Takeover Attempt A fraudster uses login details stolen from a different company's data breach to try and access a user's account on a platform like DIYAuctions.
- The Defense in Action: The system notices the login is coming from a strange device in a different city. This out-of-the-ordinary behavior is instantly flagged, triggering multi-factor authentication (MFA). A verification code is sent to the real user's phone. The criminal doesn't have the phone, so they can't get in—and the actual user gets an alert about the suspicious activity.
By seeing how specific threats are neutralized by dedicated solutions, you can understand how a layered strategy creates a powerful shield. It's how we turn abstract security ideas into practical, everyday safeguards that keep you and your money safe.
The Game-Changing Role Of AI In Detecting Fraud
If traditional fraud protection is like a security guard with a checklist, then AI is the entire forensics team working in seconds. Artificial intelligence and Machine Learning have completely flipped the script, turning static, rule-based systems into dynamic defenses that learn and adapt on their own. Think of it as a digital immune system for your finances.
This technology sifts through millions of data points in real time, hunting for subtle patterns a human analyst could never hope to spot. It connects seemingly unrelated activities—like a small login attempt from one country and a password reset from another—to uncover sophisticated fraud rings before they can do any real damage. Its ability to see what's coming is its greatest strength.
The Power Of Predictive Analysis
AI doesn't just react to known threats; it anticipates new ones. By learning from every single transaction, it can identify emerging fraud tactics the moment they appear. This is especially critical for stopping complex schemes like synthetic identity fraud, where criminals build entirely new identities using a mix of real and fake information.
AI's ability to process massive amounts of data and recognize hidden connections is what makes it the cornerstone of modern fraud protection. It can tell the difference between a legitimate customer's unusual purchase and a fraudster's calculated attack.
This isn't some far-off future concept; it's the industry standard right now. In fact, a staggering 93% of organizations expect AI to redefine fraud detection, recognizing that investing in these systems is the most effective way to cut down on fraud. You can see how companies are planning their future investments in this 2025 fraud report from Alloy.
As these systems get smarter, they not only beef up security but also create a much smoother experience for honest users. This level of advanced protection is just as important for an online marketplace as it is for high-value physical assets, which is why having the right safeguards like estate sale insurance is always a smart move.
Still Have Questions About Fraud Protection?
Even when you know the basics, it's natural for a few more specific questions to pop up. Let's tackle some of the most common ones to help you feel even more confident about staying safe online.
Is Fraud Protection The Same As Antivirus Software?
Great question, and the answer is no. They protect you from completely different types of threats, and you really do need both.
Think of it like this:
- Antivirus software is the security system for your house (your computer or phone). Its main job is to stop burglars—like viruses, spyware, and ransomware—from breaking in and damaging your property.
- Fraud protection, on the other hand, is like a personal bodyguard for you and your wallet when you're out in the world. It protects your money and identity during online transactions, no matter what device you're using.
One guards your machine, while the other guards your actions and your identity across the internet.
Can I Just Rely On My Bank's Fraud Protection?
While your bank’s security is an absolutely essential layer of protection, it can only see what happens within its own walls. It has no way of knowing if a convincing phishing email tricks you into giving away a password for another website, or if your identity gets stolen from a data breach at a store you shop at.
Think of your bank's security as a strong deadbolt on your front door. True safety comes from combining that deadbolt with other smart habits, like locking your windows (using unique passwords) and not opening the door to strangers (being wary of unsolicited requests).
When you combine your bank's efforts with your own awareness, you create a much stronger shield than any single system can offer alone.
What Is The Single Most Important Habit For Preventing Fraud?
If you were to focus on just one thing, it would be this: adopt a "trust but verify" mindset.
Almost every scam relies on creating a sense of urgency or panic to rush you into making a mistake. The most powerful defense is simply to pause, take a breath, and independently check out any unexpected request for your money or information.
For instance, if you get a frantic text from a family member asking for money, don't reply directly. Call them on the phone number you already have for them. If your bank sends an urgent-sounding email, don't click the link inside. Instead, open a new browser tab and go directly to their official website or app to see if there are any real alerts. This simple habit pulls the rug out from under nearly every scammer's strategy.